Review every change without adding headcount
Neo monitors all changes automatically. No more scavenger hunts across docs, tickets, and code. Security teams get continuous signal without scaling linearly with engineering.
Neo learns your architecture, APIs, and trust boundaries, then keeps threat models current as your system evolves. Security teams move at engineering speed.
Neo treats threat modeling as a continuous engineering control, not a periodic exercise. It produces artifacts leadership can trust and findings engineers can act on.
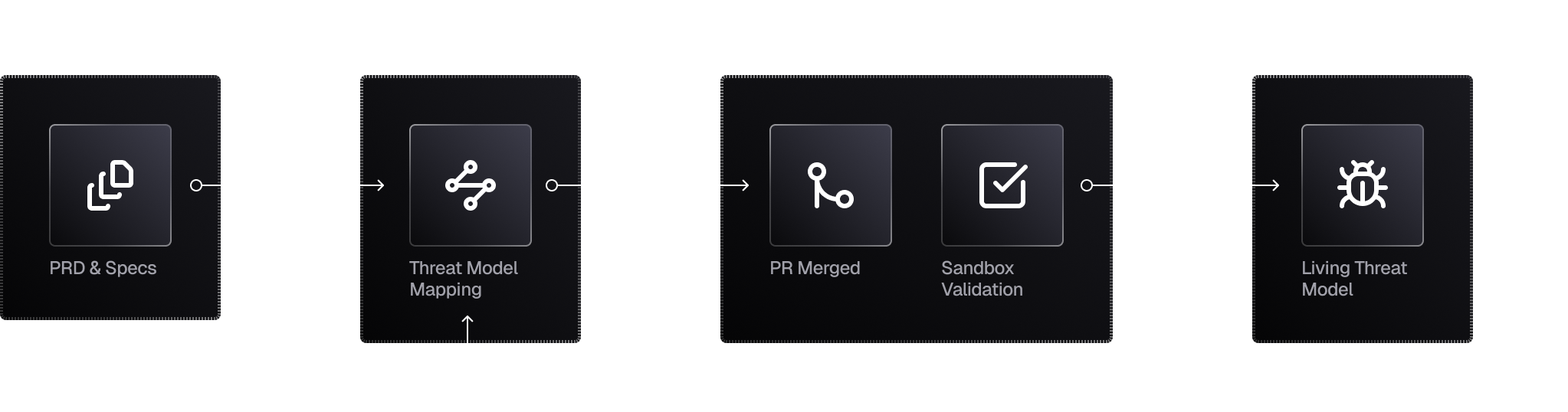
Neo ingests design docs, API specs, and architecture diagrams to map trust boundaries before code is written.

As PRs merge and code ships, Neo updates the threat model automatically, highlighting what changed and where new attack paths appear.

Neo understands how your application behaves and generates abuse cases accordingly. Authorization gaps, data exposure risks, workflow manipulation.

Neo generates test cases from identified threats and validates them against developed code in sandboxed environments. You get evidence of what is actually exploitable.

Past decisions, accepted risks, and architectural context persist. Every review builds on what Neo already knows. Versioned artifacts for audit and compliance.

Neo starts from your architecture docs, updates as code ships, and validates threats at runtime. The result is a threat model that evolves with your system.
Proven exploitability, standardized analysis, built-in compliance.
Neo monitors all changes automatically. No more scavenger hunts across docs, tickets, and code. Security teams get continuous signal without scaling linearly with engineering.
Same rigorous analysis every time, not dependent on who is available or how busy the sprint is. Neo applies the same threat modeling standards across every feature and every team.
Sandbox validation confirms what is actually vulnerable. Theoretical risks get separated from confirmed threats with reproduction steps and evidence attached.
Versioned artifacts that evolve with your system. Threat models are saved as persistent files with every change tracked for audit, compliance, and leadership visibility.