Pentesting that gets smarter with every run
Neo remembers your architecture, your business logic, and what it found last time. Every engagement builds on the last, so your security posture compounds instead of resetting every quarter.
Your team is triaging noise,
not fixing what's exploitable
Security tools and pentests weren't built for modern engineering velocity. One generates noise, the other is a quarterly snapshot. Exploitable vulnerabilities slip through, and your security team is left being a bottleneck or a rubber stamp.
Less time for real threats
SAST, DAST, SCA. Every tool adds to the pile, and most findings are unactionable without manual verification. Over time, teams learn to ignore alerts they can't easily prove. The real vulnerabilities get buried alongside the noise.
Stale on arrival
By the time the pentest report lands, your codebase has moved on. Quarterly engagements capture a snapshot that's outdated within weeks. Attackers don't wait for your next engagement window.
No memory, no compounding
Every new vendor starts from scratch. They don't know your architecture, your business logic, or what was found last time. You're paying for the same ramp-up every cycle while past fixes go unverified.
What pentesting looks like
when it actually works
Not a checkbox you tick quarterly. Pentesting that keeps pace with every release, proves exploitability, retests your fixes, and becomes a continuous part of how you ship securely.
Every finding proven exploitable
No theoretical risk ratings. Every vulnerability comes with a working exploit, full HTTP traces, and reproduction steps. Your team triages facts, not assumptions.
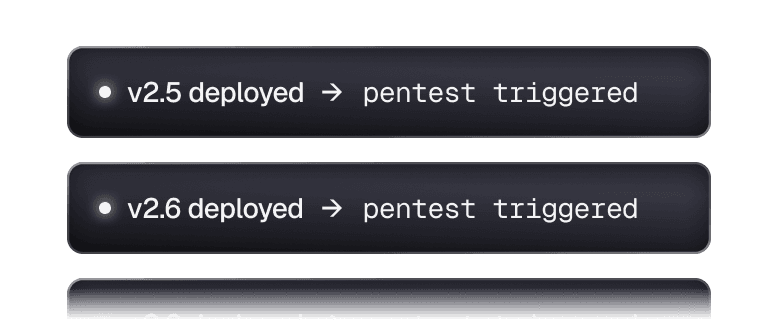
Test after every deploy
Run on your schedule, not a quarterly calendar. After every release, after every infrastructure change, or on-demand when your team needs confidence.
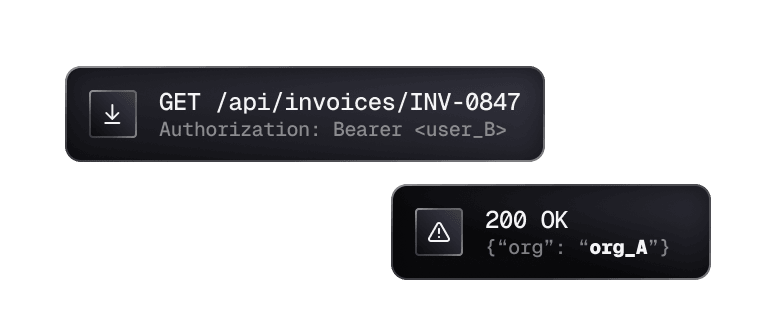
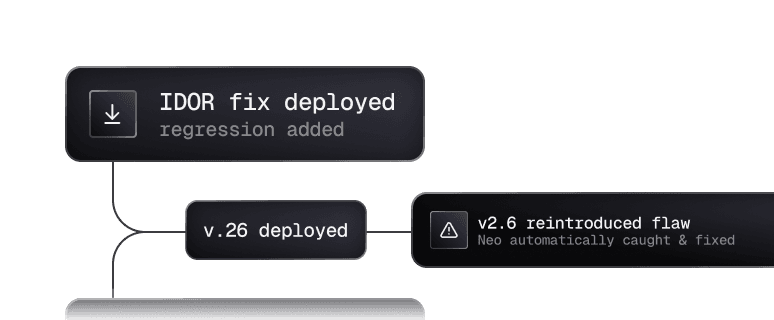
Fixed vulnerabilities stay fixed
Every finding becomes a permanent regression check. When code changes, past exploits are retested automatically. No more hoping last quarter's fix still holds.
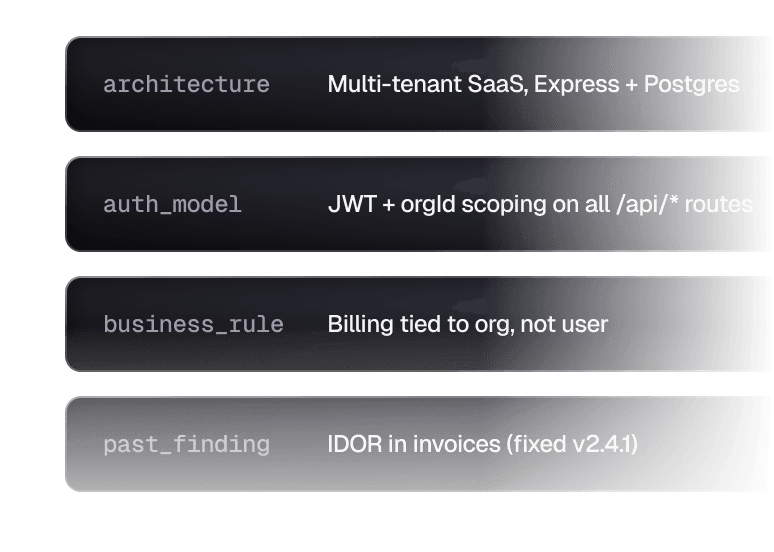
Knows your business, not just your stack
Neo carries your architecture, business logic, user roles, and past findings across every engagement. It tests like someone who actually understands how your application works. Because it does.
New threats covered in hours
100K+ security researchers contribute vulnerability knowledge to ProjectDiscovery's open-source ecosystem. When a new CVE drops, detection is often available within hours, not weeks.

Nothing in your stack goes untested
Web apps, APIs, mobile, network, cloud, source code, DNS, and business logic. Tested together, in context, from one platform. No blind spots between tools.
| Attack surface | Neo | XBOW | Terra | Pentera | Horizon3 |
|---|---|---|---|---|---|
| Web applications | |||||
| APIs (REST, GraphQL) | |||||
| Business logic | |||||
| Mobile applications | |||||
| Internal network | |||||
| Cloud infrastructure | |||||
| Source code / PRs | |||||
| DNS / subdomain | |||||
| Compliance |