Table of Contents
Authors
Imagine discovering that your company's login credentials are sitting in plain sight on the internet, accessible to anyone who knows where to look. Unfortunately, this isn't hypothetical – it's happening right now to organizations worldwide through malware-stolen credentials.
The Hidden Threat: Malware-Stolen Credentials
Every day, cybercriminals deploy malicious software that quietly steals passwords from infected computers. These "stealer" programs harvest credentials from browsers and applications, then bundle this data into logs that often end up publicly accessible on the internet. Your employees' devices can become unknowing sources of your organization's most sensitive access credentials.
Real-World Impact: When Leaked Credentials Turn Into Disasters
Healthcare Under Attack: The 2023 MOVEit Transfer attacks affected multiple healthcare organizations, with initial access often gained through compromised credentials (CISA Advisory). According to IBM's Cost of a Data Breach Report 2024, healthcare breaches cost an average of $11.05 million per incident, with many traced back to credential-based attacks.
Financial Sector Breaches: The 2022 Lapsus$ group attacks on major financial institutions began with stolen employee credentials obtained from malware infections (Microsoft Security). These incidents resulted in unauthorized access to customer accounts and significant regulatory penalties.
Manufacturing Shutdowns: The 2021 Colonial Pipeline ransomware attack, which disrupted fuel supplies across the Eastern United States, began with a single compromised password. The six-day shutdown cost the company millions and affected millions of consumers.
Small Business Devastation: According to the 2024 Verizon Data Breach Investigations Report, 86% of breaches at small businesses involve stolen or weak credentials, with many companies never recovering from the financial and reputational damage.
Infostealers Evolve Quickly: In 2025, infostealers can turn stolen logins and session cookies into turnkey initial access. Ankura’s JD Supra piece (Aug 19, 2025) stresses that modern stealers quietly harvest credentials and session cookies, which can bypass MFA via session hijacking.
Why Organizations Need Credential Monitoring
Your organization faces this threat because employee devices get infected and people reuse passwords across personal and work accounts. Remote work further increases risk by expanding access from unmanaged devices and unsecured networks.
The stakes are high: regulatory fines, lost customer trust, business disruption, and financial damage. The faster you identify exposed credentials, the better you can protect your organization.
The Solution: ProjectDiscovery's Free Credential Monitoring
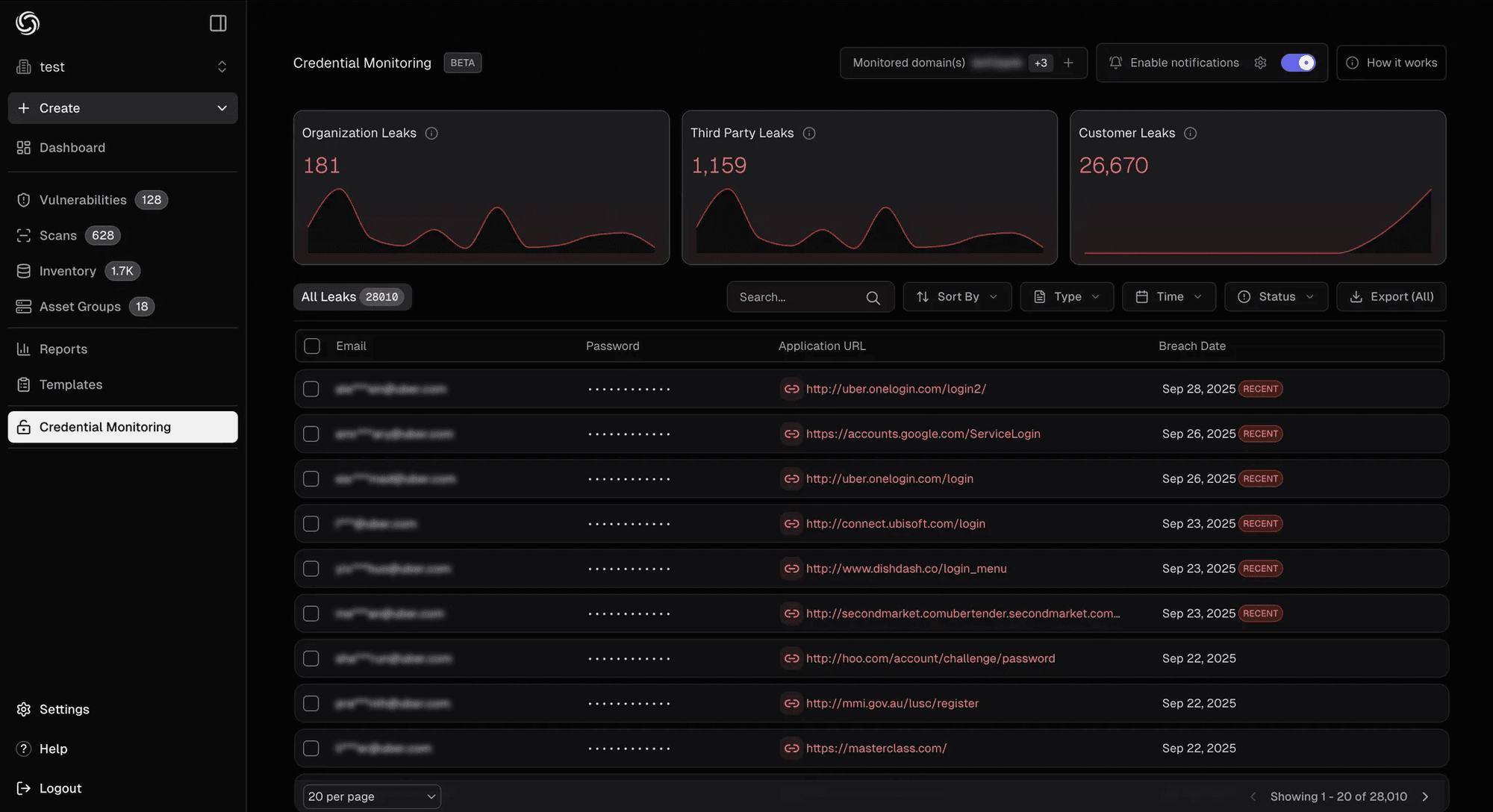
Our credential monitoring solution continuously scans, ingests, and parses publicly accessible malware logs for your organization's credentials, providing real-time alerts when exposures are discovered.
Try It Now
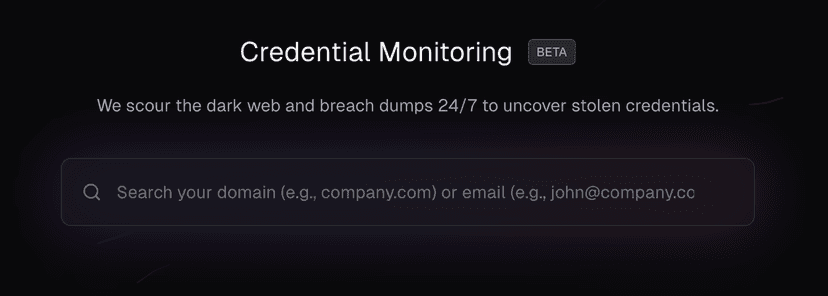
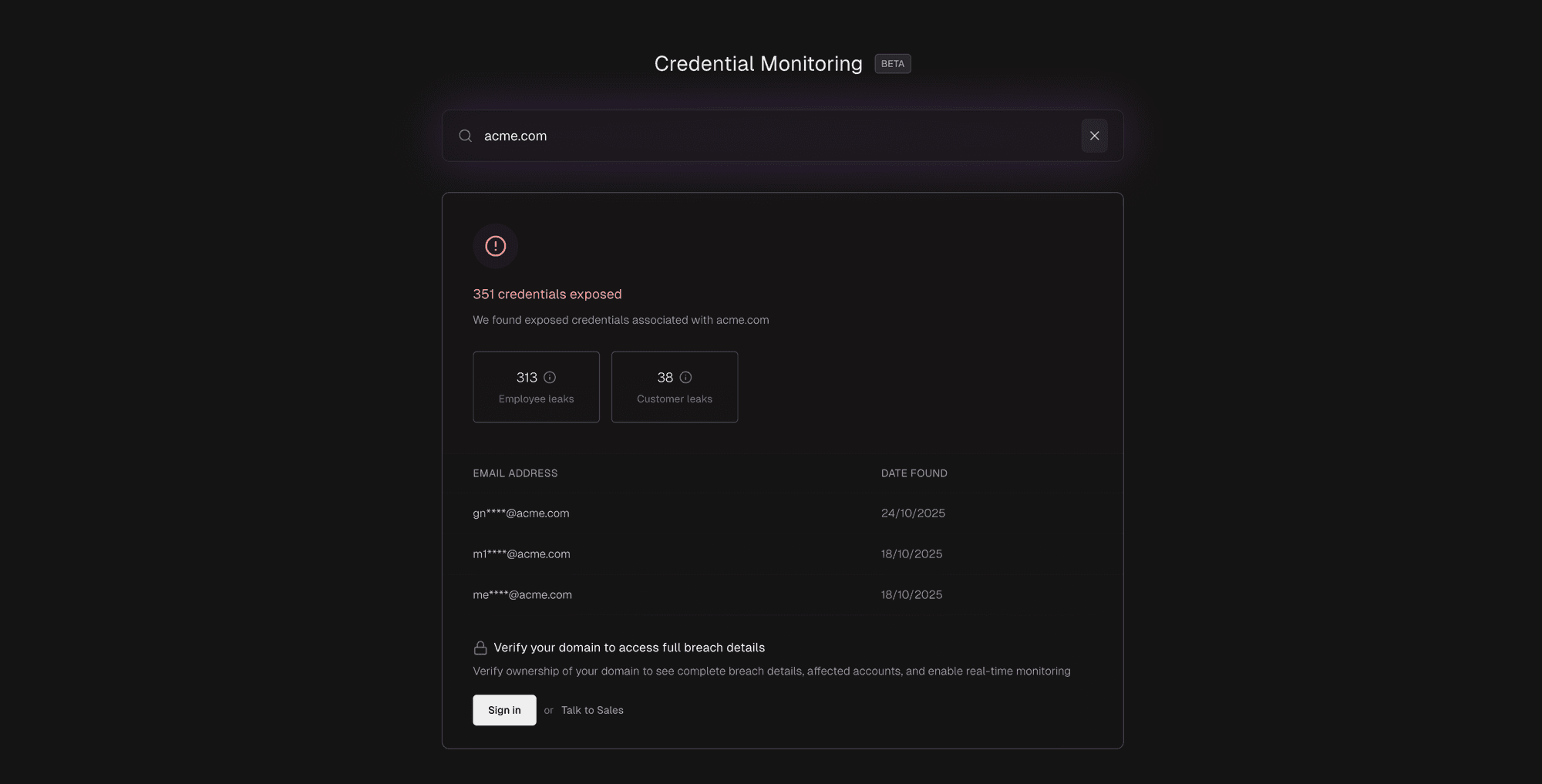
Visit cloud.projectdiscovery.io/leaks and perform an initial search without creating an account to see if your credentials are already exposed.
Free for Everyone
Individual Users: Monitor personal email addresses, receive alerts for new exposures, export data, and access our API integration.
Business Domains (Free with Domain Verification): Monitor all employee emails, view exposed passwords, track customer credential exposures, and export comprehensive security reports.
Enterprise Solutions: Multi-domain monitoring, priority support, enhanced reporting, and custom API integration for larger organizations requiring advanced capabilities.
Getting Started
Immediate Assessment: Visit cloud.projectdiscovery.io/leaks and search for your email or domain to reveal existing exposures.
Create Free Account: Sign up to enable continuous monitoring, real-time alerts, and detailed exposure reports.
Verify Domain (Business Users): Unlock organization-wide monitoring and customer credential tracking by verifying domain ownership.
Take Action: Reset affected passwords immediately, enable multi-factor authentication, and notify affected users when exposures are found.
Learn More: Read our Credential Monitoring Docs for detailed information on this feature.
Start Protecting Your Organization Today
Start with a Free Search – See what's already exposed
Sign Up for Free Monitoring – Get ongoing protection and alerts
Learn More – Explore technical details and setup guides
Remember: in cybersecurity, prevention is always better than recovery. The credentials protecting your organization are already being targeted – make sure you're the first to know when they're compromised.
Ready to secure your organization? Visit cloud.projectdiscovery.io/leaks and discover what credentials might already be exposed. Your first search is free, and ongoing monitoring costs nothing for most users and businesses.


